A medieval Engish castle that relies on a perimeter moat and strong walls for defense
In enterprise networks in the past, we relied heavily on network segregation to protect corporate assets, information and systems. The theory was pretty simple: Build a wall putting good guys on the inside and the great unwashed on the outside, and then carefully control what comes in and goes out through gateway(s).
Mobile devices and cloud are now forcing enterprises to move from traditional network design with perimeter moat and strong walls for defense of internal network.
Zero trust is where there is no difference between the internet and the intranet.
BeyondCorp, coined by Google, arose from an internal initiative to get rid of Google’s traditional perimeter VPNs and privileged networks after the Aurora attacks of 2009. BeyondCorp espouses 3 core principles:
BeyondCorp, coined by Google, arose from an internal initiative to get rid of Google’s traditional perimeter VPNs and privileged networks after the Aurora attacks of 2009. BeyondCorp espouses 3 core principles:
- Connecting from a particular network must not determine which services you can access.
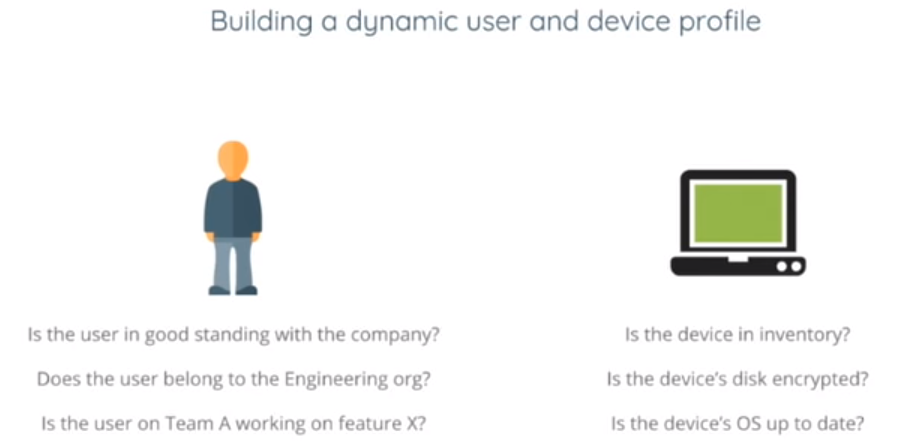
- Access to services is granted based on what we know about a user and the device.
- All access to services must be authenticated, authorized and encrypted.
https://storage.googleapis.com/pub-tools-public-publication-data/pdf/45728.pdf


Zero Trust Security, coined by Forrester’s John Kindervag who foresaw breaches like the one at Target in 2013, promotes replacing open network designs with one focused on segmentation and central management. Core Zero Trust recommendations include:
- Ensure all resources are accessed securely regardless of location
- Adopt a least-privileged strategy and strictly enforce access control
- Continuously monitor the ecosystem

Architecture diagrams for BeyondCorp (left) and ZeroTrust (right) security initiatives
As you can see in their respective architecture diagrams above, although BeyondCorp sought to replace the VPN while ZeroTrust pushed for stronger segmentation with Next-Gen Firewalls, both concepts essentially say the same thing:
- Do not rely on location and perimeter for security
- Enforce granular access controls based on context
- Continuously monitor and adapt your security policies
No comments:
Post a Comment